Use cases of services
Applications and Real-World Examples
- Home
- Use Cases
Fraud management TELCO
Identity Guard
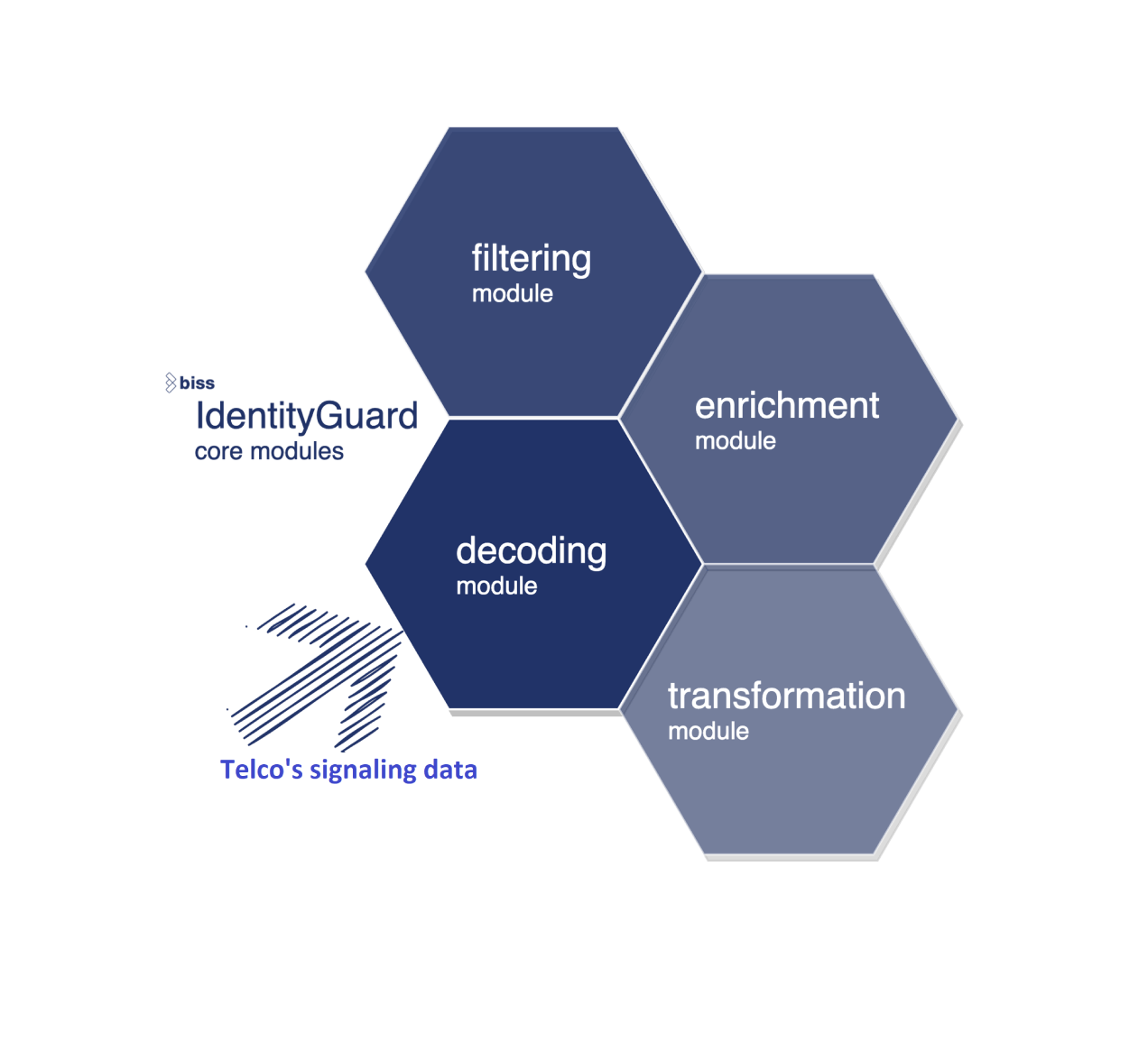
Decoding of network signal data, process them and provides transformed data to defined systems in near real-time frame. Multiple integration types including messaging brokers (Kafka/RabbitMQ), SFTP, REST. High scalability (both horizontal and vertical).
Telco Fraud Challenges
Fraud costs the telco industry an estimated €10 billion per year according to a 2019 report by Europol’s European Cybercrime Centre.
Identity Guard
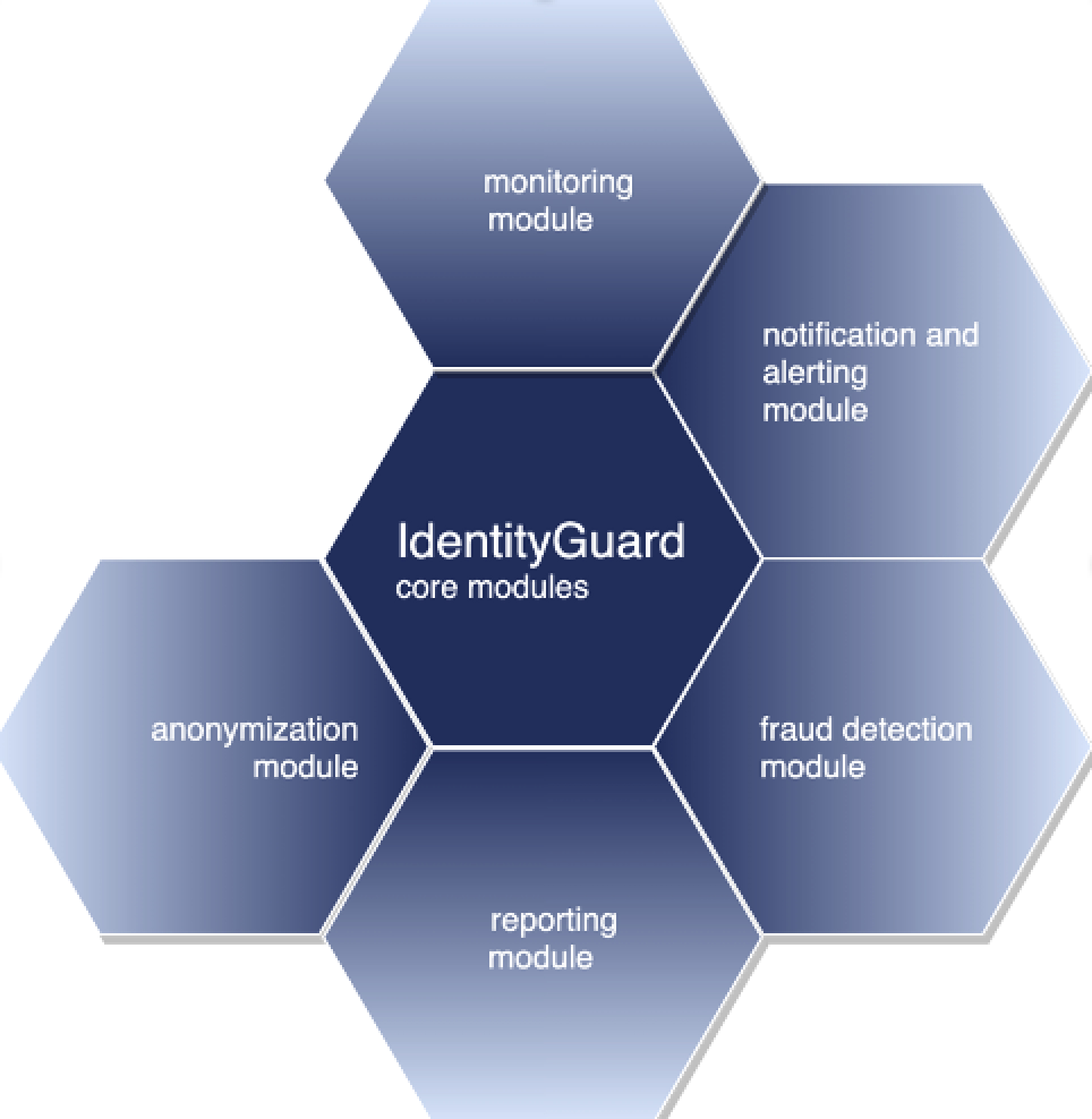
Product overview: Monitoring, Reporting, Notification and alert, Fraud detection, Anoymization.
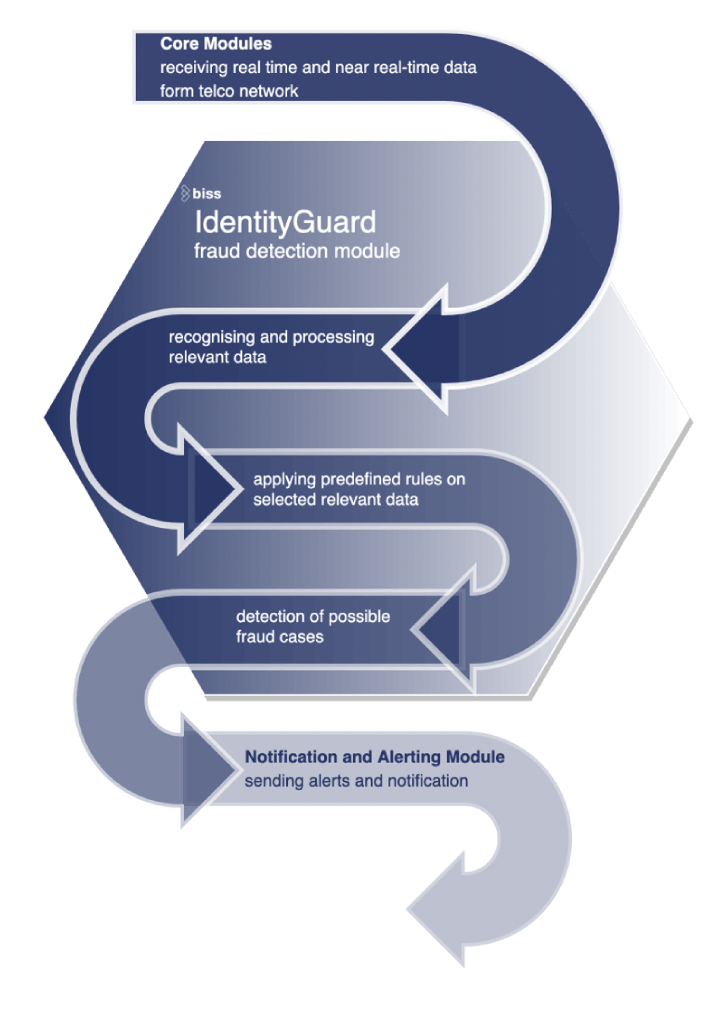
Fraud detection module: Seamless integration, Supports three mayor telecommunication fraud types, Possibility to add new fraud rules, Support of fraud detection exclusion list.
Fraud management TELCO
Fraud Detection Module
According to a Europol’s Europian cybercrime centre, fraud costs the telco industry around €10 billion per year and the amount rises constantly.
In 2020 SMS phishing attacks skyrocketed by more than 328%. Fraudsters use different methods which target both MNOs as well as customers and vary from infrastructure attacks to social engineering attacks.
Wangiri attacks
Zero-duration calls, mostly to mobile devices, that leave a missed-call number, which is either a premium rate number or one that produces advertising messages
In more recent cases, bots or scripts initiate fraud by filling out a company’s online form with information that leads the companies to call back premium numbers
FRAUD MANAGEMENT TELCO
Fraud detection rules
-
Wangiri - zero-duration calls, mostly to mobile devices, that leave a missed-call number, which is either a premium rate number or one that produces advertising messages
-
Wangiri 2.0 - bots or scripts initiate fraud by filling out a company's online form with information that leads the companies to call back premium numbers.
-
SMS Spam & Phishing - sending mass SMS in order to obtain personal information from the person who receives the messages
-
Interconnect Bypass - using SIM cards from a local carrier and rerouting international calls using a SIM box or GSM gateway
-
List of risk countries / operators with defined threshold limit
Fraud detection module
According to a Europol’s Europian cybercrime centre, fraud costs the telco industry around €10 billion per year and the amount rises constantly. In 2020 SMS phishing attacks skyrocketed by more than 328%. Fraudsters use different methods which target both MNOs as well as customers and vary from infrastructure attacks to social engineering attacks. Wangiri attacks Zero-duration calls, mostly to mobile devices, that leave a missed-call number, which is either a premium rate number or one that produces advertising messages In more recent cases, bots or scripts initiate fraud by filling out a company’s online form with information that leads the companies to call back premium numbers. Interconnect bypass Using SIM cards from a local carrier and rerouting international calls using a SIM box or GSM gateway SMS Spam & Phishing Sending mass SMS in order to obtain personal information from the person who receives the messages
Fraud detection module
According to a Europol’s Europian cybercrime centre, fraud costs the telco industry around €10 billion per year and the amount rises constantly. In 2020 SMS phishing attacks skyrocketed by more than 328%. Fraudsters use different methods which target both MNOs as well as customers and vary from infrastructure attacks to social engineering attacks. Wangiri attacks Zero-duration calls, mostly to mobile devices, that leave a missed-call number, which is either a premium rate number or one that produces advertising messages In more recent cases, bots or scripts initiate fraud by filling out a company’s online form with information that leads the companies to call back premium numbers. Interconnect bypass Using SIM cards from a local carrier and rerouting international calls using a SIM box or GSM gateway SMS Spam & Phishing Sending mass SMS in order to obtain personal information from the person who receives the messages
Movement Analytics
The movement analytics portal visualizes anonymized users paired with user attributes. The Source of the geospatial information can be massive data produced by mobile network or different process-related data which can be obtained from other sources. Source data is anonymized near the source to satisfy GDPR requirements.
Our solution can use attributes and enrich location information with data from other systems like CRM or any ICT solution that provides adequate API. The final visualization is multidimensional and can be tailored to the customer’s needs. Obtained results of the analysis are delivered as customized graphs and reports.
Use Case
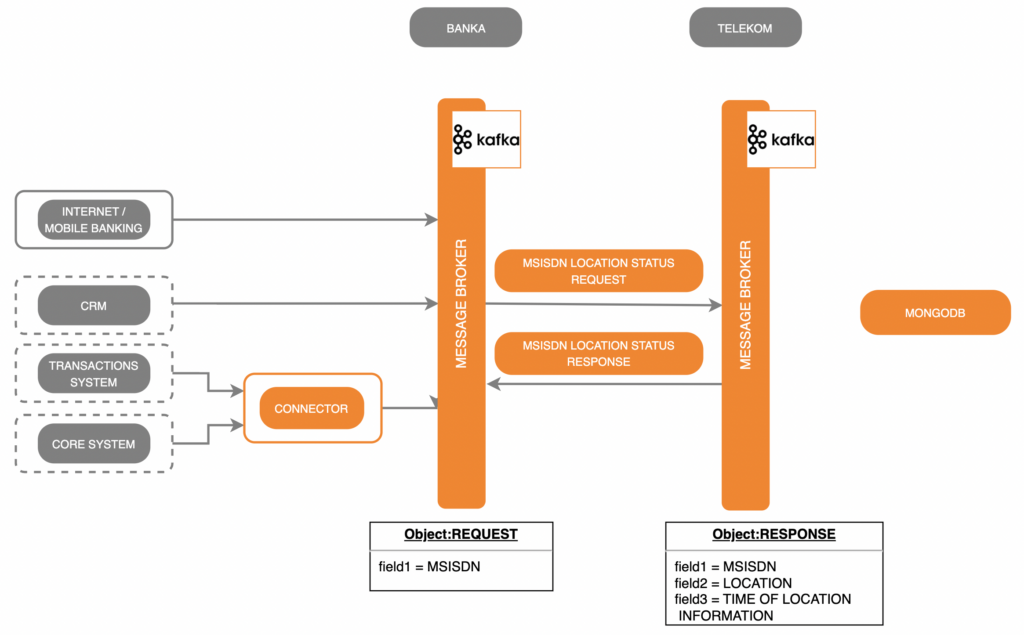
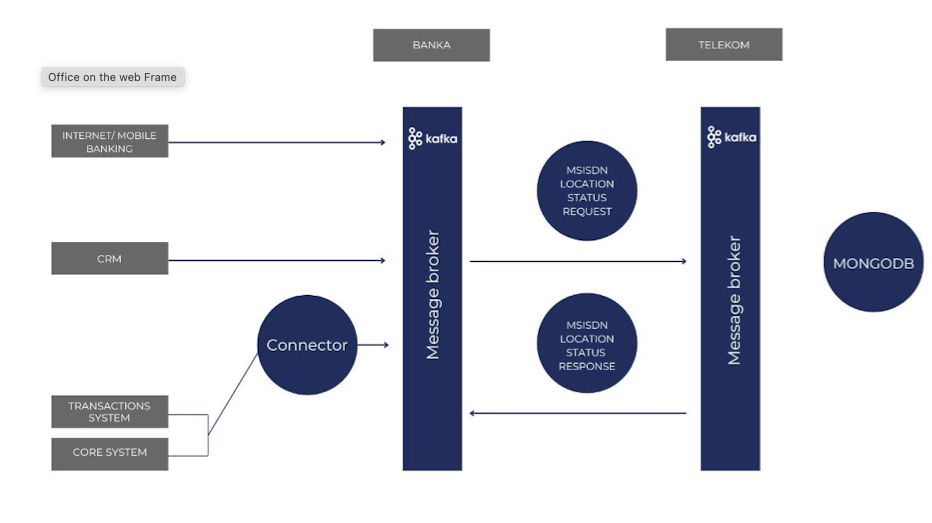
By connecting the current position of the bank card and mobile device location, our system can add a valuable additional parameter to the bank’s fraud management systems. GDPR Compliant. Anoymized data. Connecting card and mobile device location. Configurable.
Example
The mobile device location is somewhere in the city of Zagreb, while the EFTPOS transaction is being made in the greater Dubrovnik area. The transaction is recognized as possibly unauthorized and the PIN code is required even if the transaction is under 250 HRK or a contactless transaction
Movement analytics
-
Heat maps - See it at a glance - heat map view provides an intuitive view of required data
-
Multidimensional attributes - Know it all - multidimensional attributes are covering all the information required
-
Anonymization - Control reverse anonymization of PII data securely
-
Reporting - An extensive and customizable reporting engine will keep you up-to-date at all times
Movement analytics
The movement analytics portal visualizes anonymised users on a heatmap paired with user attributes. The source of the geospatial information can be massive data produced by mobile networks or different process-related data which can be obtained from other sources. Source data is anonymised near the source to satisfy GDPR requirements. Our solution can use attributes and enrich location information with data from other systems like CRM or any ICT solution that provides adequate API. The final visualisation is multidimensional and can be tailored to the customer’s needs. Obtained results of the analysis are delivered as customised graphs and reports. Example usage is tourist movement reported by tourist nationality in a particular area.
Heat maps
Anonymization
Multidimensional attributes
Reportions
Get Started
Are you interested in this and do you see a possible application?
Get in touch with us and find out more.